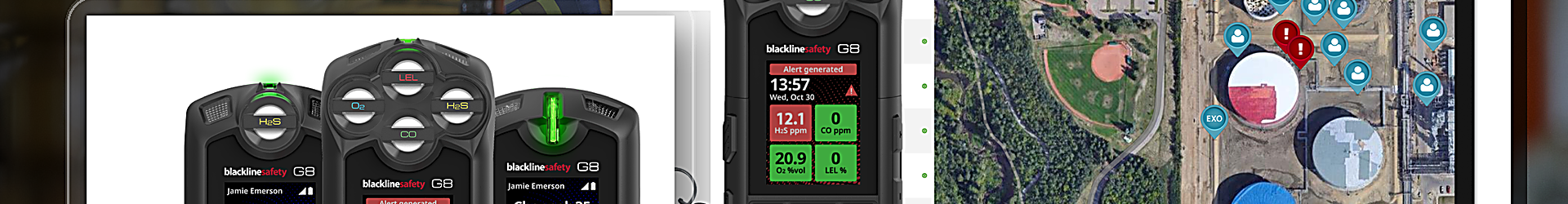
Artificial intelligence (AI) may be powerful, but it is vulnerable to cyber threats. In health care, the consequences of a cyberattack can be deadly. Organizations seeking to implement this technology securely should follow these cybersecurity guidelines to preserve patient outcomes. 1. Utilize Input Filtering In a prompt injection attack, a […]