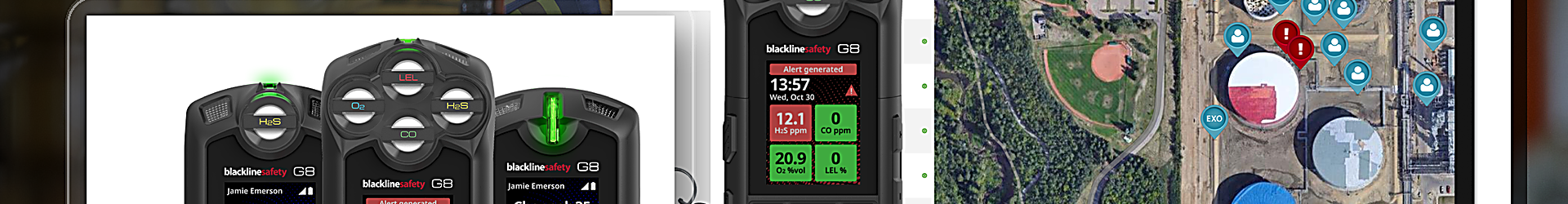
Biometric authentication relies on unique physical and behavioral traits, such as fingerprints, facial recognition and voice patterns, to verify identity. This method presents a more formidable alternative to traditional passwords and PINs, effectively reducing the risks of unauthorized access and data theft. However, while biometrics offer a stronger security measure, […]