Security teams have more than enough data telling them what’s wrong; they just don’t have enough telling them what’s the most wrong.
Which is where exposure assessment platforms (EAPs) come in.
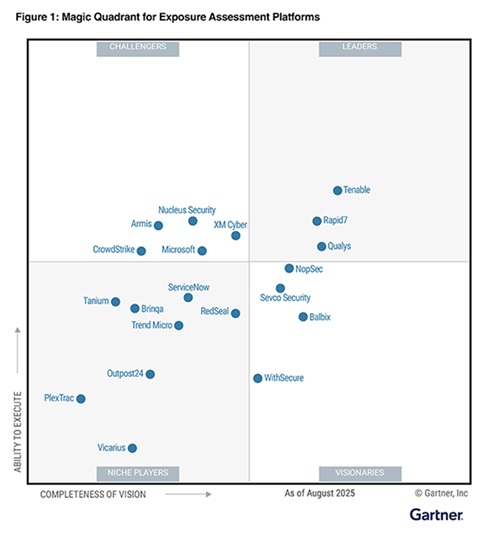
Gartner formally recognized the importance of EAPs in its inaugural Magic Quadrant for EAPs, a landmark milestone for the industry, especially as it replaced the long-standing Market Guide for Vulnerability Assessment.
That’s because SOCs don’t need another laundry list of vulnerabilities. They need a comprehensive, continuous overview of all assets and their weaknesses so they can prioritize fixes based on impact.
And that’s exactly what exposure assessment platforms do, making them essential to modern cybersecurity strategies today.
Cyber Exposure Management: Embracing the Shift
The landscape is changing rapidly for security practitioners, with new SaaS solutions, APIs, BYODs, virtual machines, and identities being added every day. These new additions bring with them new risks. Point-in-time solutions aren’t made to keep up.
Threat management needs to move with the times, because as one SANS instructor put it, “attackers aren’t waiting for your quarterly scan.” The answer is continuous threat exposure management (CTEM), and exposure management platforms are the tools that make it happen.
Exposure management relies on understanding business context, the regulatory environment, and the threat landscape. Then, once those pieces are understood, discovering all areas exposed to threat and prioritizing them based on their total impact on the business. CTEM does this on an ongoing basis (the “continuous”).
Here is a summary of the exposure management shift, and why the market winds are changing:
- No more point-in-time: This is a marked shift from a cadence of quarterly scans, which give attackers a twelve-week head start if they time things right.
- No more SOC burden: It also represents a shift from SOCs doing all the work of prioritizing threats, to automation and AI doing that work for them.
- No more single puzzle pieces: It represents a shift from being presented with a bunch of disparate (yet possibly prioritized) puzzle pieces, like in an advanced vulnerability scan, to being presented with real-world, simulated attack path scenarios discovered by AI.
- EAPs probe threat exposures and leverage AI to determine the myriad ways attackers could infiltrate from there.
- Once discovered, those attack paths are neatly packaged and delivered to human SOC analysts for immediate action and impact.
As new assets get added and new threats appear, teams need to be able to discover assets and weaknesses, prioritize remediations, and action mitigation just as fast.
And Gartner would agree.
Why Gartner Created a Magic Quadrant for EAPs
Gartner’s rollout of the Magic Quadrant for EAPs is significant not only because it introduces a new market category, but because it takes the place of the (now defunct) Market Guide for Vulnerability Assessment.
Vulnerability Management Is Outdated
It’s true: vulnerability management as we know it is outmoded. According to Gartner, “By 2027, organizations that integrate exposure assessment data into IT and business workflows will experience 30% less unplanned downtime from exploited vulnerabilities than those relying on isolated vulnerability management tools.”
Exposure management solutions provide leveled-up vulnerability management that goes beyond finding weaknesses alone; it identifies how they impact the business and prioritizes them accordingly. Not based on severity score alone, but based on context:
- Likelihood of getting breached
- Sensitivity of the asset
- Severity of the vulnerability
- Impact to the bottom-line
- Regulatory consequences and fines
This multi-point approach underscores current industry trends to meld current cybersecurity tactics with overarching business priorities. No more “security in a vacuum.”
Using VM as a Springboard to CTEM
However, vulnerability management programs do tend to be the most mature out of cybersecurity initiatives, so experts recommend using your established VM program as a jumping-off point. You want to move from siloed VM to cross-domain exposure management, which means expanding it to include:
- All asset types
- All risk types
- All security policies
- All workflows
Across your entire attack surface.
How EAPs Enable Continuous Threat Exposure Management
EAPs do the heavy lifting of making continuous, comprehensive visibility and threat prioritization happen across complex and distributed environments. They are the solutions that make CTEM happen.
There are five stages to the continuous threat exposure management process: scoping, discovery, prioritization, validation, and mobilization, as listed below. EAPs play a significant role in three: discovery, prioritization, and validation. Here’s how it all fits together.
- Scoping: Decide what you will and will not include in your CTEM program. Business stakeholders are central to this process, as they will determine which systems and Tier 1 elements are absolutely critical. Once business priorities have been established, security can flesh out the technical “how” details from there.
- Discovery: EAPs build a trusted, unified asset inventory to serve as the foundation for prioritized attack path mapping later on. This covers asset information, including:
- Vendor
- Users
- Type
- Software
- Configuration
- Risks
It also includes pre-build cyber-hygiene policies to track common problems and deal with common issues.
- Prioritization: EAPs prioritize exposures based on common criteria across domains (business impact, likelihood of exploitation, severity score, etc.) and highlighting visible attack paths.
- Validation: Once priorities have been established, they need to be validated to see if they need to be moved up or down. For example, a gap in access controls may be low on the list until you validate the IAM policy recently implemented and find it was misconfigured; now it’s time to escalate.
- Red teaming and penetration testing can help in this process.
- Mobilization: EAPs give you real-time visibility into zero days for immediate remediation. Dashboards aligned with key business-centric KPIs. Threat investigation to provide SOCs with risk intelligence and context for faster hunting.
Why This Matters for Your Cybersecurity Strategy
Vendor sprawl is rampant. Alert volumes are so high they’re getting ignored, SOCs still struggle to see the big picture, and security teams struggle to staff.
Exposure management platforms tighten your cybersecurity strategy by the way they solve these problems:
- Letting you keep your current security investments
- Aggregating telemetries from all tools into one place
- Prioritizing remediation based on the most business-centric threat – eliminating noise and overwhelm
And lastly, EAPs help SOCs with stretched resources and limited expertise by using GenAI to provide plain-English explanations to step-by-step attack chain mitigation prompts.
Gartner’s Magic Quadrant for EAPs signals a major market shift. It offers security leaders a clear view of their options and an unbiased comparison of vendors, helping you see who is driving exposure management forward and why it matters.
As organizations struggle with the speed and scale of modern threats, yesterday’s solutions won’t keep pace. The industry is reshaping around modern cybersecurity solutions like CTEM and exposure management; security leaders should seek to follow suit.
About the Author:
An ardent believer in personal data privacy and the technology behind it, Katrina Thompson is a freelance writer leaning into encryption, data privacy legislation, and the intersection of information technology and human rights. She has written for Bora, Venafi, Tripwire, and many other sites.
.
.
Additional Resource
Video Overview
Follow Brilliance Security Magazine on LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information. BSM is cited as one of Feedspot’s top 10 cybersecurity magazines.