Listen to the article
In an era where cyber risks evolve as quickly as technology itself, alignment among technology leaders — including chief information officers (CIOs), chief technology officers (CTOs) and chief information security officers (CISOs) — has become a strategic necessity. When these leaders share a unified vision for security strategy that supports broader business goals, organizations strengthen resilience, improve decision‑making and turn security into a competitive advantage.
Why Leadership Alignment Matters
Cybersecurity cannot remain isolated within IT departments. Today’s threat landscape affects every facet of an organization — from customer trust to market reputation to operational continuity. A strategic cybersecurity program requires integration with broader business objectives, not merely a set of reactive technical controls.
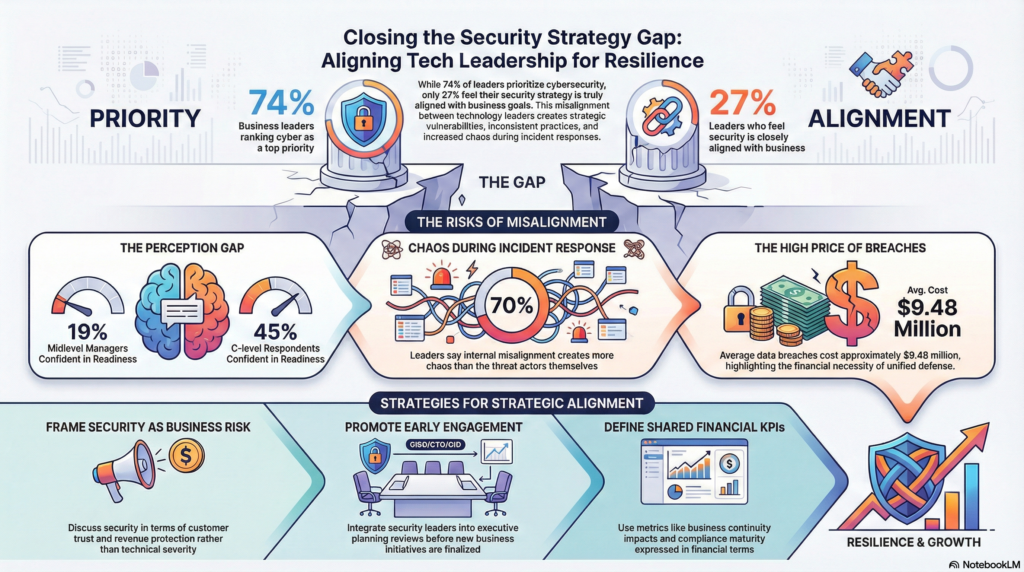
Research shows that despite cybersecurity being a stated priority for many organizations, alignment between cybersecurity strategy and business strategy remains limited. While 74% of business leaders rank cybersecurity as a top priority, just 27% feel that their security strategy is closely aligned with broader business objectives, highlighting a significant strategic gap. This disconnect illustrates how the technical and executive perspectives on cybersecurity often drift apart, creating strategic gaps that threat actors can exploit.
Defining Strategic Alignment in Practice
Alignment means more than holding periodic meetings between tech leads. It requires a cohesive approach where:
- Security is a foundational part of business planning, not an afterthought.
- Technology and security decisions are evaluated through the lens of business risk and impact, rather than solely on technical severity or compliance checklists.
- Security leaders can articulate risk and value in business language, enabling executive stakeholders to make informed, strategic decisions.
When these elements come together, organizations can prioritize security investments that protect critical assets — such as customer data, proprietary systems and operational infrastructure — while enabling innovation and strategic growth.
The Consequences of Misalignment
Misalignment among technology leaders and other executives introduces several risks.
Conflicting Priorities and Fragmented Goals
CIOs focus on business processes, CTOs on innovation and CISOs on risk management. Without a shared strategy, priorities can conflict, leaving security gaps. In smaller organizations, one person may wear multiple hats, which can streamline decisions but also blur security ownership unless responsibilities are clearly defined.
Inconsistent Security Practices
When tech leaders disagree on policies or standards, the result can be inconsistent practices across teams and environments. This inconsistency makes enforcement difficult, and gaps often surface where security controls should be strongest.
Reduced Organizational Resilience
The inability to unify leadership around security strategy weakens incident response and recovery capabilities. Disjointed plans can slow down critical decision‑making when rapid action is required, increasing the potential damage from breaches.
Perception and Communication Gaps
Recent industry surveys reveal growing perception gaps between leaders and security teams. In one survey, 45% of C-level respondents said they were confident in their organization’s readiness, but only 19% of midlevel managers said the same. Such divergent perceptions erode trust and amplify risk exposure.
Strategies for Enhancing Alignment
Bridging strategic divides requires intentional, structured efforts that bring tech leadership together with business goals. Here are practical steps security professionals can champion.
Establish a Unified Security Vision
Craft a strategic cybersecurity roadmap that aligns with organizational objectives. This roadmap should articulate how security initiatives directly support outcomes — such as revenue protection, operational continuity, regulatory compliance and reputation management — rather than presenting security in purely technical terms.
Define Shared Metrics and Key Performance Indicators (KPIs)
Translate security outcomes into metrics that resonate with business leaders. This includes showing mean time to detect (MTTD) threats, business continuity impacts and compliance maturity in financial terms. Shared KPIs create a common language that facilitates better governance and investment decisions.
Encourage Cross‑Functional Accountability
Use governance frameworks that clarify responsibilities among the CIO, CTO, CISO and other stakeholders. This reduces role ambiguity and encourages collaboration by aligning leadership to strengthen decision‑making, risk management and overall security posture. It’s similar to purple teaming that integrates offensive and defensive teams to reduce breaches, which cost about $9.48 million on average.
Craft Risk‑Driven Conversations
Frame security discussions around business risk, such as customer trust erosion or potential losses from service outages, rather than focusing solely on technical vulnerabilities. This approach resonates better with executives and aligns security priorities with overall risk appetite and resource planning.
Promote Early Engagement With Executive Leadership
Security leaders must be present during executive planning and strategic reviews. Early involvement ensures that cybersecurity considerations are integrated into new business initiatives, rather than appended after decisions are made. Notably, 70% of security leaders report that internal misalignment generates more chaos during incident response than the threat actors themselves, emphasizing the importance of coordinated leadership.
Alignment as a Strategic Imperative
When tech leaders share goals, speak a common language of risk and collaborate effectively, security transforms from a constraint into a strategic enabler. Security professionals can drive this alignment through early engagement, shared metrics and risk-focused dialogue — ensuring security supports innovation, business priorities and long-term resilience.
Devin Partida is a frequent contributor to Brilliance Security Magazine, an industrial tech writer, and the Editor-in-Chief of ReHack.com, a digital magazine for all things technology, big data, cryptocurrency, and more. To read more from Devin, please check out the site.
.
.
Additional Resources
Video Overview
Follow Brilliance Security Magazine on LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information. BSM is cited as one of Feedspot’s top 10 cybersecurity magazines.


