Healthcare networks hold some of the most sensitive information. Patient records, medical devices and clinical applications are a pot of gold for hackers. Any gap in defenses can result in serious risks to patient safety and data privacy. A zero-trust security model can help protect personal information, allowing the hospital to focus on saving lives.
What Is Zero Trust?
Zero trust is a security model that assumes no user, equipment or connection is trustworthy without authentication — even if it’s already inside the network. For hospital teams, it means maintaining strict access controls and visibility to protect client data and the vital systems that keep clinics running.
Implementing Zero Trust in Healthcare Facilities
Here’s a roadmap for hospitals to adopt zero-trust measures. Each step helps strengthen security while supporting the critical work healthcare teams do every day.
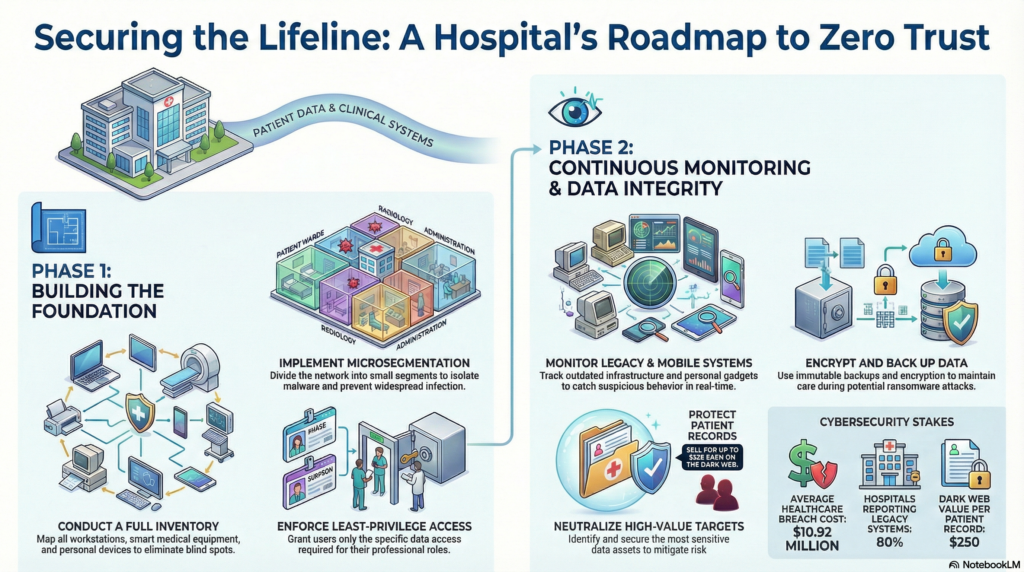
1. Start With a Full Inventory
The first step is to identify all official devices on the network. This includes everything from workstations to smart medical equipment. Mapping how each gadget communicates with other instruments helps create policies that protect without disrupting essential systems.
A common entry point for attackers is through unmanaged Internet of Medical Things (IoMT) equipment, which often goes unnoticed and creates blind spots. The legacy machines that comprise this framework no longer receive essential security patches, which makes it vulnerable to modern cyber threats. Additionally, bring-your-own-device (BYOD) programs can create security vulnerabilities if personal gadgets lack proper protection.
2. Microsegment the Network
Instead of a single, flat network where malware can roam freely, zero trust calls for dividing the infrastructure into multiple smaller segments. If one device or department gets infected, microsegmentation keeps the problem isolated.
This containment strategy is pressing because healthcare has faced some of the most expensive breaches in 2024, with each incident costing an average of $10.92 million. Beyond the dollars, every minute of downtime disrupts patient care. Quick and precise threat isolation can become a matter of life and death.
3. Enforce Least-Privilege Access
Every user, hardware and application should have only the access needed to complete their specific tasks. For example, doctors shouldn’t have the same permissions as contractors, and the billing department should not have access to HR systems. When this principle is combined with continuous verification and multi-factor authentication, it ensures that no one can access information or platforms beyond their authorized scope.
4. Keep an Eye on Devices
Medical devices are lifesavers, but they can also be the weakest link in the healthcare system. In the U.S., many hospitals still run on legacy systems. A survey shows that 80% of respondents consider outdated infrastructure the norm. This perspective passively puts patient data at risk.
Mobile devices and medical apps used by doctors may also be unsecured. In 2015, 80% of physicians relied on these tools to make care more efficient, and this number has only increased since then.
Zero-trust security requires constant monitoring of how both outdated and personal devices behave on the network. Specialized tools track the activity of every machine to ensure it doesn’t compromise the entire architecture.
For example, if a diagnostic machine suddenly tries to connect to a strange or unknown external address, the system will spot this suspicious behavior. When something unusual is detected, the tools can automatically isolate the device to prevent potential harm. This real-time tracking gives IT teams a chance to catch problems early, before they spread and cause bigger damage.
5. Encrypt and Monitor Patient Data
Patient information is worth a fortune on the dark web, selling for up to $250 per record. Protecting this data requires more than just controlling who has access to it. Hospitals must classify, encrypt and continuously monitor digital assets to ensure their security. Whether a doctor pulls up records on official medical equipment or the files are forwarded to cashiering for payment, every movement must leave a traceable trail.
Constant surveillance helps flag unusual file transfers that could signal a breach. In addition, immutable backups and staged recovery plans can ensure that if ransomware strikes, hospitals can quickly restore care without losing critical information.
Making Zero Trust Work for Healthcare
No hospital can perfectly lock down every device or network component, especially with legacy systems and clinical demands. Still, zero trust helps shrink attack surfaces and slow down intruders. Each small step makes it harder for ransomware or hackers to spread and cause harm.
With patient safety on the line, zero trust shifts the conversation from whether a breach might happen to how the hospital can respond effectively. This mindset enables healthcare organizations to keep their data secure and patients protected.
As the Features Editor at ReHack, Zac Amos writes about cybersecurity, artificial intelligence, and other tech topics. He is a frequent contributor to Brilliance Security Magazine.
.
.
Additional Resource
Video Overview
Follow Brilliance Security Magazine on LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information. BSM is cited as one of Feedspot’s top 10 cybersecurity magazines.


