Organizations opt for multiple cloud platforms primarily for flexibility and resilience. They distribute workloads across different providers and avoid vendor lock-in. However, the more a company uses best-of-breed services for each need, the wider the attack surface becomes. How should IT teams balance these challenges while continuing to reap the perks of a multicloud environment?
What Is a Multicloud Environment?
Using a virtual, internet-based space where employees can access on-demand resources is an example of cloud computing. When a company relies on two or more of these services, it uses a multicloud environment. About 62% of organizations have already adopted such architectures, as these provide flexibility in selecting specialized services from each provider.
It also improves resilience since multistorage means multiaccess. Even if one vendor experiences an outage, employees still have options and can continue working. This flexibility is crucial because IT downtime can cost businesses $9,000 per minute, with unexpected and longer blackouts proving even more costly. Fortunately, these expenses can be minimized by planning disruptions during times that have the least impact on people’s jobs.
This also means there’s no vendor lock-in — workloads, data and applications are not tied to a single provider’s pricing or policies, which can be limiting for companies handling various kinds of work. Since there are plenty of options, businesses also get to compare and choose the most cost-efficient pricing model for them.
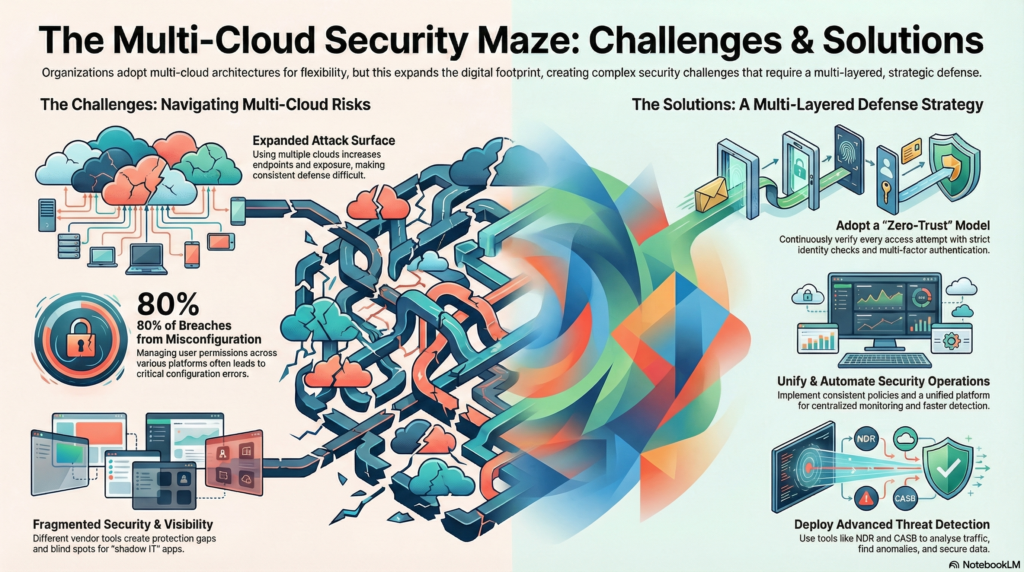
Top Network Security Challenges in a Multicloud World
While multiple options certainly open doors to significant benefits, they also complicate cybersecurity. Here’s where issues arise.
Expanded Attack Surface
Using multiple platforms expands the number of endpoints and environments that need protection. This increases exposure and makes it hard to maintain consistent defense across all clouds.
Inconsistent Security Controls
Each vendor uses different security tools. As a result, teams struggle to detect threats across all clouds because visibility becomes fragmented. Protection may be uneven, and if some components are weaker than others, it can compromise overall integrity.
Complex Identity and Access Management
A larger organization may have to manage user permissions across various platforms, which can lead to misconfiguration and privilege errors. Misconfiguration remains the cause of about 80% of multicloud breaches.
Data Compliance Risks
Data stored across different clouds must follow varying compliance requirements and encryption standards. Poor segmentation or overly permissive network rules can also allow attackers to move laterally once one environment is compromised.
Operational Overhead
Managing multiple clouds requires more skills, tools and oversight. Staff may also deploy shadow IT services without the official IT team’s knowledge. This easily creates blind spots for weak or missing security controls.
Effective Strategies to Enhance Network Security
A multicloud architecture necessitates a multilayered approach to ensure each vulnerability is covered. Here’s what IT teams can do.
1. Streamline Security Operations
Implementing consistent policies across all clouds simplifies management and reduces gaps. Using unified security platforms enables centralized monitoring, faster anomaly detection and more efficient reporting. Automation and AI accelerate vulnerability assessments. What used to be performed only once every few years for mere compliance now requires less effort, allowing teams to focus on critical threats and improve response times.
2. Employ Strong Encryption Practices
Encrypting data both in transit and at rest is a standard best practice to protect sensitive information. Centralized key management is crucial for keeping encryption keys secure and controlling access, thereby reducing the risk of unauthorized data exposure.
3. Adopt Zero-Trust Security Principles
Zero-trust architecture requires continuous verification of every access attempt, regardless of origin. Applying strict identity verification, multifactor authentication and granular access controls lets organizations limit lateral movement within cloud environments, reducing potential damage from breaches.
4. Deploy Advanced Network Detection and Response (NDR) Tools
Traditional cloud flow logs provide limited insight. NDR platforms analyze network traffic in depth, identifying unusual patterns or behaviors indicative of attacks. These tools integrate with cloud-native security solutions, improving visibility and enabling faster threat detection.
5. Address Shadow IT With Cloud Access Security Brokers (CASB)
Companies use an average of 110 different cloud platforms, which makes managing security complex. Adding to this challenge, unsanctioned applications, also known as shadow IT, create blind spots that increase risk. To address this, CASB solutions help by monitoring app traffic, finding unauthorized apps and enforcing security rules to close those gaps before attackers can take advantage.
6. Collaborate With Managed Security Providers
Cybersecurity talent shortages make outsourcing to managed security service providers (MSSPs) a practical option. These bring specialized expertise, 24/7 monitoring and advanced tools that help maintain a strong and proactive defense posture across complex multicloud environments.
Multilayered Protection for Multicloud Integrations
Multicloud environments offer undeniable advantages, but they require a careful protection strategy that focuses on visibility, control and automation. Fortunately, with unified policies and advanced detection tools, businesses can effectively manage network security risks and protect their digital assets, regardless of the cloud infrastructure they use.
As the Features Editor at ReHack, Zac Amos writes about cybersecurity, artificial intelligence, and other tech topics. He is a frequent contributor to Brilliance Security Magazine.
.
.
Additional Resource
Video Overview
Follow Brilliance Security Magazine on LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information. BSM is cited as one of Feedspot’s top 10 cybersecurity magazines.


