By Zach Norton, Digital Marketing Specialist and Expert Writer at Pentest-Tools.com
To mitigate the damage of Slowloris attacks, increase bandwidth, adjust hardware configuration, broaden your infrastructure, and invest in DDoS mitigation software and hardware.
One of the most common cyberattacks is a Distributed Denial of Service (DDoS) attack. A DDoS attack attempts to prevent legitimate users from accessing a website or other network service.
About the Slowloris DDoS Attack
The Slowloris DDoS attack is a simple denial of service attack that works by sending a large number of HTTP requests to a web server. The bogus traffic can be sent from one or multiple sources, either over the internet or from a local network, and is typically sent to a single target.
The traffic is sent at a rate that is significantly higher than the target’s ability to handle, which causes the target to become unavailable to its legitimate users.
The goal of a DDoS attack is to take a target offline, or at least to make it so that its users are unable to access its services. This type of attack can also be used in conjunction with ransom notes.
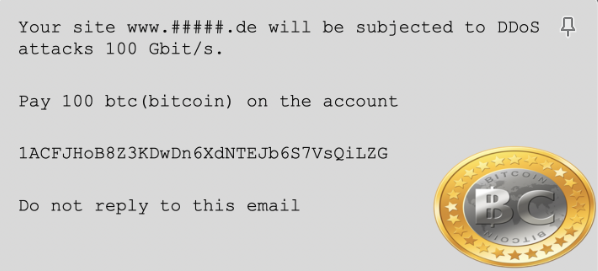
Website owners may be asked to pay for the attackers to stop the DDoS attack, often by transferring bitcoin to a specific account.
This is a real ransom note from 2012, when the closing price for bitcoin was just $13.45. Based on today’s bitcoin price, this would be asking for more than $3,800,000.
The Slowloris attack is fittingly named after a slow-moving primate found in Southeast Asia. This DDoS attack moves slowly and waits for sockets to release before consuming them.
As an application layer DDoS attack, Slowloris uses partial HTTP requests to open connections between the source and the target web server. It keeps these connections open for as long as possible to slow the server down. Other ports and services are not affected by this attack.
Cybercriminals may use a botnet to issue a Slowloris attack so that the traffic looks legitimate. Android and IoT device botnets have increasingly become a threat to cybersecurity.
For Android botnets, users install a substantial number of applications on their devices from a variety of sources. Malicious software can be installed on an Android device while users download applications intended for other reasons, such as media players or ringtone downloaders.
For example, in 2017, the WireX botnet which consisted of at least 70,000 concurrent IP addresses from 100 countries was uncovered. Approximately 300 apps in the Android Play Store were identified as affected and removed from devices and the app library.
Typically, large organizations have been targeted with Slowloris attacks, but many possible motives exist to target smaller organizations.
Slowloris attacks are often used in conjunction with other types of attacks such as SQL injection or cross-site scripting. Let’s take a closer look at how to mitigate Slowloris attacks.
How to Mitigate Against Slowloris
Slowloris DDoS attack is effective against a variety of web server software but is particularly effective against Apache 1.x and 2.x.
1. Increase bandwidth
The most basic solution to handle malicious spikes in traffic is to buy more bandwidth. However, increasing bandwidth can almost seem like a battle of attrition and many organizations might not want to scale up bandwidth to defend against volumetric attacks.
This method of defense might work best for larger organizations that can allocate enough resources to network bandwidth to absorb DDoS attacks. Monitoring traffic for spikes and reacting in times of attack are still necessary even with increased bandwidth.
2. Adjust hardware configuration
Configuring your hardware to defend against cybersecurity threats is key in DDoS attack mitigation. Consider limiting the number of connections that can be made by a client per IP address. However, limiting the number of connections per IP address is an effective way to mitigate against Slowloris DDoS attacks from one source.
As well, set timeouts for receiving HTTP request headers and bodies from clients. If a client does not send any header or body data within the determined time then a timeout error is sent by the server.
Disabling ICMP entirely won’t necessarily improve security. Network administrators might be inclined to disable ICMP in an effort to obscure certain elements, however, this method only makes network monitoring more difficult. Consider blocking some inbound and outbound ICMP instead of disabling entirely.
3. Broaden your infrastructure
Prevent single sources of failure on your site. If your website and web servers are running only on DNS servers without redundancies in place, it is possible that a failure could bring down your entire site. Ensure that your servers are spread across multiple data centers to discourage attackers.
Each of the data centers needs to be connected to different networks for this method to be effective. Servers that are distributed geographically can make it more difficult for attackers to successfully execute a Slowloris attack.
A load balancer can be used to distribute traffic across multiple servers. This is a good way to prevent single points of failure. A hardware load balancer can be set to accept only complete HTTP connections.
With this, all packets are inspected for completeness before being forwarded to the web server. Apache also comes with mod_reqtimeout to specifically protect against application-layer attacks.
4. DDoS mitigation software and hardware
DDoS mitigation software can be used to defend against Slowloris attacks. A firewall can be used to protect your network from malicious traffic. Firewalls are designed to block all incoming and outgoing traffic that is not explicitly allowed.
Additionally, network traffic analysis can be used to detect and mitigate DDoS attacks. It is also possible to identify points of weakness using a vulnerability scanner.
Content delivery networks (CDNs) are a service for handling significant amounts of traffic from legitimate sources. However, CDNs are also a popular method for mitigating DDoS attacks.
A cached version of your website is stored and provided to user requests. The load is taken off of the server so high traffic volume, legitimate or not, won’t overwhelm the server.
Zach Norton is a digital marketing specialist and expert writer at Pentest-Tools.com, with several years of experience in cybersecurity, writing, and content creation.
.
.
Follow Brilliance Security Magazine on Twitter and LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information.