Rezonate Free Scan Tool Reveals Vulnerabilities
By Peter R. Kelley
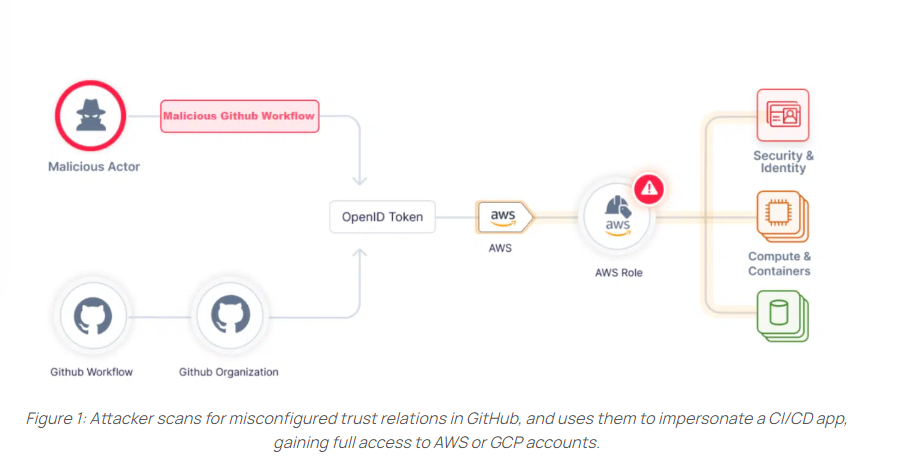
Rezonate researchers have just published findings showing that user organizations’ misconfigurations of GitHub OpenID (OIDC) integrations with their cloud-native vendors – AWS and Google – continue to put many organizations at risk of account takeover attacks.
Findings in From GitHub To Account Takeover: Misconfigured Actions Place GCP & AWS Accounts At Risk include:
- Misconfigurations identified across various organizations – Rezonate researchers found many such misconfigurations in a scan of 1500 vulnerable service accounts across GCP and AWS
- A step-by-step guide for discovering and fixing the problem(s)
- A free scan tool that lets users determine whether their organizations’ GitHub content is vulnerable to account takeover and immediate remediations to take.
Rezonate CEO Roy Akerman said, “The problem is in AWS & GCP Configuration that misconfiguring leads to potential account takeover if exploited. We have found dozens of organizations that are dealing with it. These real-life cases triggered this research.”
GitHub Warns of Potential for Misconfigurations
GitHub notes that although the integration between the cloud and GitHub is relatively simple, potential misconfigurations could expose access to unauthorized parties.
GitHub articles refer to Conditional access as part of the integration process. However, the cloud infrastructure is not flagging or alerting when conditional access is not being used.
GitHub also warns that the lack of notification from the cloud provider during the setup increases the chances that an organization will have misconfigured trust settings. Those misconfigurations may result in roles and service accounts that can be abused by threat actors/attackers, leading to unauthorized access.
GitHub specifies two types of misconfigurations that can be exploited by attackers to gain unauthorized access to a trusted cloud account.
Misconfiguration – Lack of Subject Condition occurs when the user who integrated the role did not add conditional limitations to cloud access. This misconfiguration allows any GitHub organization to access the cloud account.
Misconfiguration – Poorly-Defined Condition Pattern occurs when the conditions defined limit the subject but are not restrictive enough and thus can be bypassed.
In addition to its research, Rezonate published an open scan tool to spot and address OpenID misconfiguration-related vulnerabilities. “Every organization can take action today – against both public and private resources to assess risk and their optimal fix steps.”
Follow Brilliance Security Magazine on Twitter and LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information.

