Cybercriminals have ramped up their attacks on Ukrainian citizens in the wake of the Russian invasion of Ukraine.
According to a new blog post from The Media Trust, there has been a five-fold increase in malware targeting Ukrainian consumers since the start of the conflict.
“The writing was on the wall in the lead up to the military invasion of Ukraine. Typically experiencing a handful of consumer-directed attacks each month, the country endured a 2X malware surge towards the end of December. The cyber assault continued past the February 24 invasion reaching 5X through April.,” said Chris Olson, CEO, The Media Trust.

Olson warned, “Concerns of propaganda and disinformation propagation are natural elements of cyber warfare. Attacks on infrastructure targets are to be expected. The role consumers play is often overlooked: their devices are targeted with investigative malware that roots around for valuable information—credentials, system access, contacts, and more—that is then leveraged in future attacks. This is precisely what’s happening in Ukraine.”
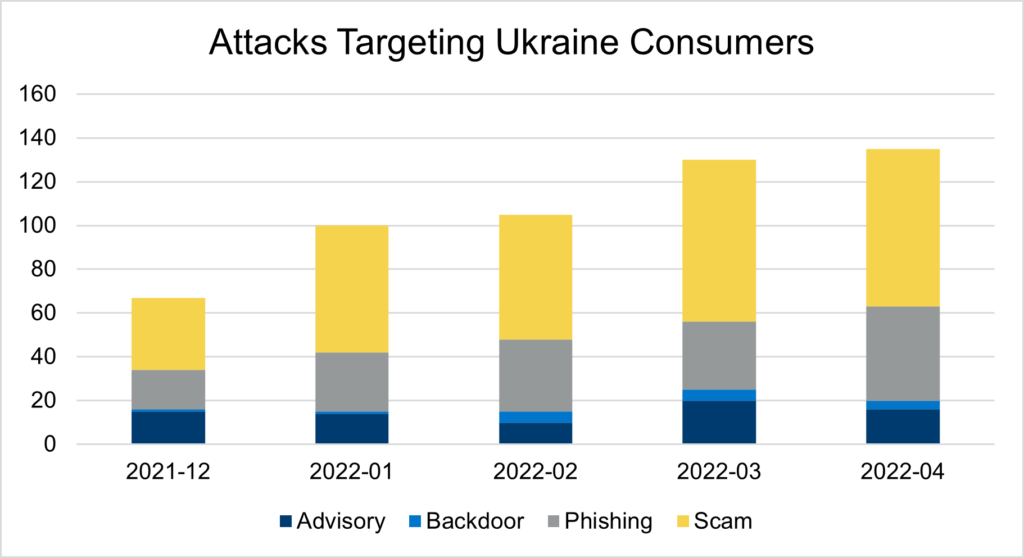
The malware targeting Ukrainian devices is telling. The malware’s attack analysis shows that it identifies people, either directly through credential collection or indirectly via device information gathering. A study of attacks from January through April shows the following:
- Scams, 54%. Credential collection. These are generally phishing/credential theft attempts that seek to obtain personal information from clients before using it to harass them in the future.
- Phishing/malicious: 28%. This malware attacks by using pop-ups, browser hijacks, and fraudulent surveys. These fraudulent surveys are a scam designed to get people to click on a malicious link and provide personal information. This malicious content forces the user to a new page and generates content that is difficult to erase, if possible at all.
One malware attack mentioned explicitly in The Media Trust’s blog post is GhostCat. Threat actors use third-party content (advertising, in this case) to hijack a browser and redirect to another location, which is usually dangerous. These assaults are effective since they ignore ad blocker plug-ins and creative blockers employed by ad-supported media sites such as news and media publishers.
The influx of malware has compromised individuals in Ukraine and their digital and personal security. The issue is that they are unaware of when they are being assaulted. While cryptomining and resource-intensive events drain battery life and slow performance, most malware situations are not apparent to the user. As a result, their gadgets—both personal and professional—have become identified as future targets.
Concerns about the spread of misinformation are at the top of the government’s list. But little consideration has been given to the idea that people working in sectors such as the military, government, and infrastructure are equally vulnerable as consumers. Their own devices are just as susceptible to malware. Consumers provide an opening for future, more widespread assaults once infected with malware.
The consequences of unchecked malware delivery are frightening. That’s why website/mobile app owners everywhere, but especially in war-torn areas, need to be aware of all code running on consumer devices and remove any illegal software. It’s not as difficult as it seems; just take a little time to map out the digital attack surface and react to the anomalies.
Steven Bowcut is an award-winning journalist covering cyber and physical security. He is an editor and writer for Brilliance Security Magazine as well as other security and non-security online publications. Follow and connect with Steve on Twitter, Instagram, and LinkedIn.


