The University of Phoenix has disclosed a data breach affecting nearly 3.5 million people, a reminder that when core enterprise platforms get hit, the fallout extends well beyond a single department or system. In this case, attackers exploited a critical, then-unknown vulnerability in Oracle E-Business Suite (EBS), accessed sensitive records, and extracted data tied to students, alumni, employees, faculty, and suppliers.
What happened, and why timing matters
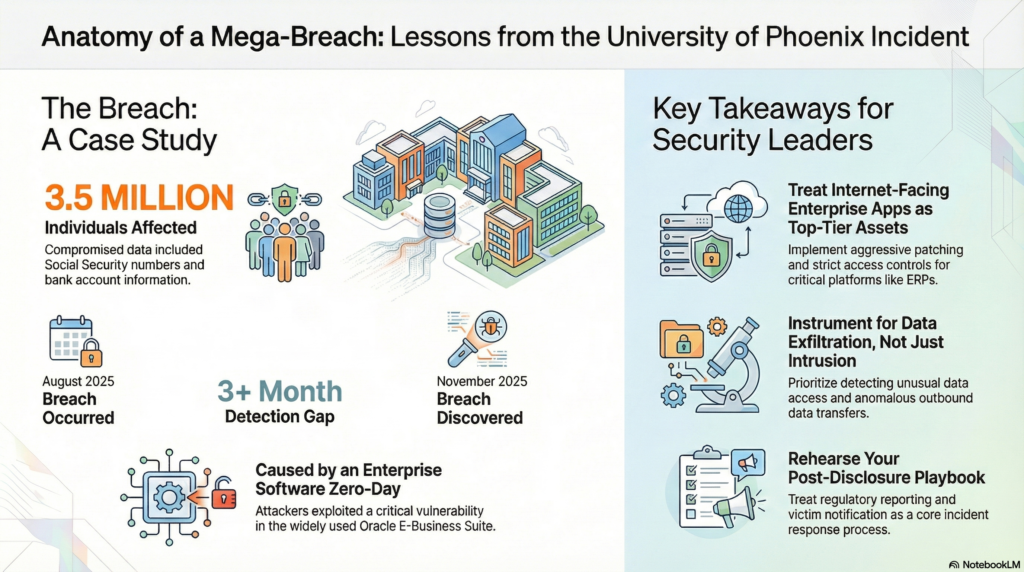
Based on an incident briefing, the unauthorized access occurred between August 13 and August 22, 2025. The university later determined that the attacker copied and exfiltrated information during that window. The total affected population is listed as 3,489,274 individuals.
The breach timeline is as consequential as the scale. The university did not detect the compromise until November 21, 2025, more than three months after the intrusion window. The briefing indicates the discovery followed public activity from the Cl0p ransomware group, which reportedly listed the University of Phoenix on its leak site.
Phoenix Education Partners, Inc., the parent company, disclosed the incident in a Form 8-K filed December 2, 2025. Broad public notification efforts began December 22–23, 2025.
For security leaders, that sequence is familiar and frustrating. When an incident is discovered late, the organization’s best options narrow. Containment becomes harder to prove, and response shifts quickly from technical remediation to crisis management, regulatory disclosure, and identity protection support for affected individuals.
What data was taken
The incident involves exfiltration of personal and financial identifiers. The compromised data included:
- Full names
- Email addresses and phone numbers
- Dates of birth
- Social Security numbers
- Bank account numbers and bank routing numbers
The university reportedly stated that bank account information was accessed “without means of access,” suggesting that credentials needed to log in to bank accounts were not part of the stolen dataset. That nuance may reduce some forms of immediate fraud, but it does not eliminate risk. When Social Security numbers and dates of birth are in play, criminals have the building blocks for account takeovers, synthetic identity creation, and targeted phishing that can follow people for years.
The technical root cause: Oracle EBS zero-day exploitation
The incident briefing ties the compromise to exploitation of CVE-2025-61882, a critical vulnerability affecting Oracle E-Business Suite versions 12.2.3 through 12.2.14. The vulnerability is described with a CVSS score of 9.8 and the ability for an unauthenticated remote attacker to compromise Oracle Concurrent Processing via HTTP, leading to remote code execution.
Oracle released patches in October 2025, and the University of Phoenix installed the patches after they became available. But patching is only part of the story here. If exploitation occurred in August, and detection did not come until late November, the patch closes the door after the data has already left the building.
The briefing also maps the incident to MITRE ATT&CK concepts, aligning the activity with initial access followed by exfiltration, including techniques associated with pulling data from Oracle EBS repositories.
Cl0p and the shift toward data theft extortion
The attack is presented as part of a broader campaign attributed to the Cl0p group, described as a Russian-speaking cybercriminal syndicate known for exploiting zero-days in widely deployed enterprise software to conduct large-scale data theft and extortion. The briefing notes Cl0p’s prior high-profile campaigns involving MOVEit Transfer, Accellion FTA, and GoAnywhere MFT.
The Oracle EBS campaign is described as affecting over 100 organizations worldwide, with other higher-education victims listed as including Harvard University, the University of Pennsylvania, and Dartmouth College.
Notably, the incident is characterized as data theft and extortion rather than disruptive ransomware deployment. The playbook is straightforward: exfiltrate first, then publicly list the victim to increase pressure to negotiate, sometimes backed by sample data posted as proof. For defenders, this model changes what “success” looks like. An organization can keep systems running yet still suffer severe harm if sensitive data is quietly extracted.
Response actions and the legal shadow that follows
After discovery, the university engaged third-party cybersecurity firms to investigate, made required regulatory filings, and began sending notification letters. For affected individuals, the university offered 12 months of identity protection services through IDX, including credit and dark web monitoring, identity theft recovery services, and a $1 million identity fraud reimbursement policy.
The parent company stated in its SEC disclosure that it believed the incident would not have a material adverse effect on business operations or student programming and indicated it maintained cybersecurity insurance to cover incident-related costs.
Even with those steps, legal pressure is typical in breaches of this size. The briefing notes that multiple law firms announced investigations that may precede class-action litigation focused on whether the university implemented “reasonable and adequate cybersecurity measures.”
Expert perspective: AI-enabled attacks and validation-first defense
In a news brief circulated in connection with the incident, Hom Bahmanyar, Global Enablement Officer at Ridge Security Technology Inc., argued the breach fits a broader pattern of accelerating cyber risk and emphasized a shift toward proactive, validation-led security programs:
“As 2025 comes to a close, it’s evident that cybersecurity attacks surged dramatically over the past year, fueled by threat actors increasingly leveraging AI to launch more sophisticated and effective attacks.
“The University of Phoenix data breach was disclosed publicly on December 21, but it will likely not be the final breach reported this year. This data breach serves as a stark reminder for security and risk management leaders that AI-driven threats can be detected accurately and in a timely manner only through the adoption of AI-powered security validation platforms. AI-powered threat exposure management is no longer a nice-to-have but a must-have.”
Whether leaders adopt that specific class of tooling or not, the operational point is hard to dispute: adversaries are moving faster, and security programs built around periodic assessment cycles struggle to keep up when exploit chains become automated.
Why higher education keeps getting hit
The briefing highlights three factors that make higher education a persistent target: data richness, legacy complexity, and detection challenges. Universities and education providers retain long-lived personal data that remains valuable for years. At the same time, mission-critical administrative platforms such as ERP systems are deeply integrated and difficult to modernize quickly, creating patch gaps. And when monitoring is tuned primarily for disruption, stealthy exfiltration can go unnoticed longer than anyone wants to admit.
What security leaders should take from this incident
The most valuable lessons are practical, not theoretical:
- Treat internet-facing enterprise apps as Tier 0 assets. Patch SLAs for externally exposed ERP components should be aggressive. Where patching cannot happen immediately, compensating controls matter, including segmentation, strict egress controls, and virtual patching or WAF rules.
- Instrument for exfiltration, not just intrusion. Bulk access patterns, unusual queries against repositories holding sensitive identifiers, and anomalous outbound transfers should be first-class detection priorities.
- Assume exploit campaigns industrialize quickly. Once a critical vulnerability becomes widely exploited, exposure windows compress. Continuous asset inventory, exposure management, and control validation become essential, particularly around identity and logging coverage.
- Rehearse the post-disclosure phase. Regulatory reporting, notification workflows, and vendor readiness for identity monitoring services should be treated as core incident response processes, not ad hoc legal tasks.
For the University of Phoenix, the incident is a reminder that “no operational disruption” is not the same as “no operational impact.” When millions of records are exposed, the downstream burden shows up in fraud risk, trust erosion, legal exposure, and the long tail of remediation.
And for the broader sector, the uncomfortable truth heading into 2026 is this: attackers are not just finding vulnerabilities. They are exploiting enterprise-scale platforms at scale, often faster than many organizations can patch, and sometimes faster than they can detect.
Additional Resource
Video Overview
Steven Bowcut is an award-winning journalist covering cyber and physical security. He is an editor and writer for Brilliance Security Magazine as well as other security and non-security online publications. Follow and connect with Steve on Instagram and LinkedIn.


