The current cybersecurity landscape has become increasingly complex, with the “castle-and-moat” strategy no longer as effective as it once was. Today, if a single employee’s home laptop is hacked, a criminal could use that connection to access a company’s most sensitive data and private files. Traditional tools like Virtual Private Networks, though effective at promoting data security, weren’t designed to handle the volume of traffic from so many locations. As a result, many organizations have adopted the Zero Trust model.
The Three Core Rules of Zero Trust
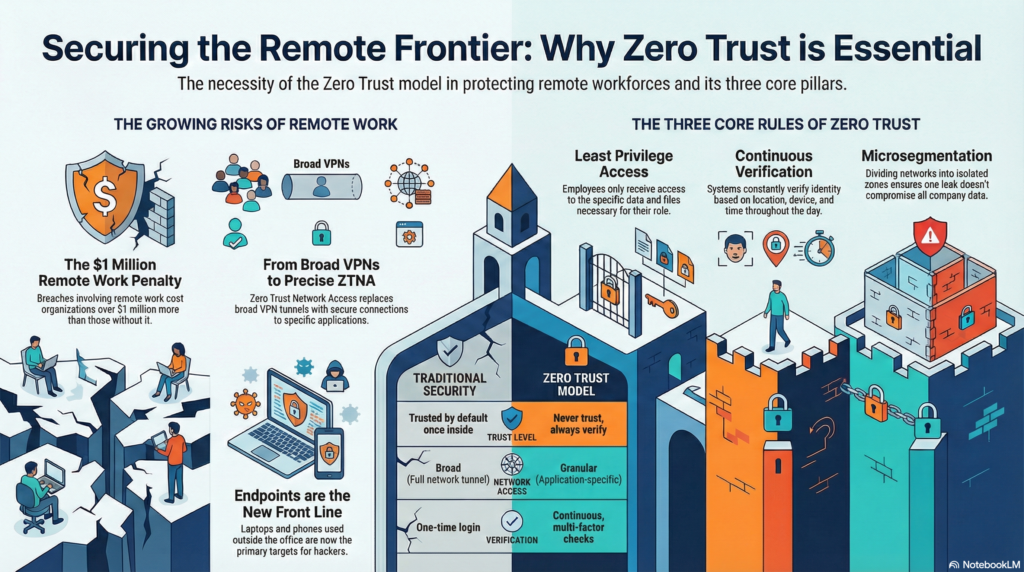
In the past, once an employee was part of the team, they were trusted with access to almost everything. While this was effective when everyone was operating in the same building at the same time, the rise of remote work post-pandemic has led many enterprises to reconsider their security standards.
Zero Trust is more of a mental framework than a specific tool or software. It follows a simple philosophy— never trust, always verify. To apply this mantra to the remote workforce, security professionals rely on three main rules.
Least Privilege Access
Under this rule, employees only earn access to pages, portals, data and files that are necessary for their role. If a team hires a new marketing intern, chances are they don’t need access to the company’s financial data. Giving the right keys to the right employees means hackers can’t move sideways through a network if they steal one person’s login.
Continuous Verification
Confirming identity should go beyond a one-time check at the start of a working day. Effective security systems constantly ensure that the user is who they say they are, looking at things like their location, their device, and the time of the day.
Microsegmentation
Dividing the network into smaller, isolated zones is a great strategy for ensuring that a leak doesn’t compromise all data. If one segment is compromised, the others remain effectively locked away.
Why Remote Work Changes the Risk
Remote work has expanded the “attack surface,” which is the total number of points where a hacker can try to break into your system. Statistics show that this risk has a real price tag. According to recent data, breaches involving remote work cost organizations over $1 million more than those without remote work.
The increased risk also raises questions about management and oversight. Leaders often wonder if remote teams can be held accountable for their security habits. Zero Trust models help solve this by requiring technical verification for every action, allowing the system to provide a clear, automated record of access. As cybersecurity attacks become increasingly advanced, comprehensive steps help managers trust their teams to work from anywhere, as the security system handles verification.
Securing Endpoints and Moving Beyond VPNs
In a Zero Trust world, the “endpoint” — which is any device an employee uses, such as a laptop or phone — is the new front line. Since these devices often operate outside the office, they are primary targets for hackers. To stay secure, organizations are replacing traditional VPNs with Zero Trust Network Access (ZTNA). While a VPN creates a broad tunnel into the entire network, ZTNA creates a specific, secure connection only to the individual application a worker needs.
It is also advisable for management teams to encourage employees to take a more active role in protecting their local environments by adopting relevant tools and fostering a culture of accountability in the workplace. Implementing smart home upgrades, such as using a separate Wi-Fi network for work devices and ensuring routers have strong passwords, adds a critical layer of defense. Training employees on basic cybersecurity awareness and practices is an absolute imperative today. When the home network is secure, the Zero Trust system has a much easier time verifying and protecting.
A Necessary Evolution
The shift to a remote workforce has made Zero Trust an essential requirement rather than an optional feature. By focusing on continuous verification, restricted access and device security, businesses can protect their data in an increasingly hostile digital landscape. While the move away from traditional perimeters takes time and effort, the result is a more secure and accountable organization.
Devin Partida is a frequent contributor to Brilliance Security Magazine, an industrial tech writer, and the Editor-in-Chief of ReHack.com, a digital magazine for all things technology, big data, cryptocurrency, and more. To read more from Devin, please check out the site.
.
.
Additional Resource
Video Overview
Follow Brilliance Security Magazine on LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information. BSM is cited as one of Feedspot’s top 10 cybersecurity magazines.


