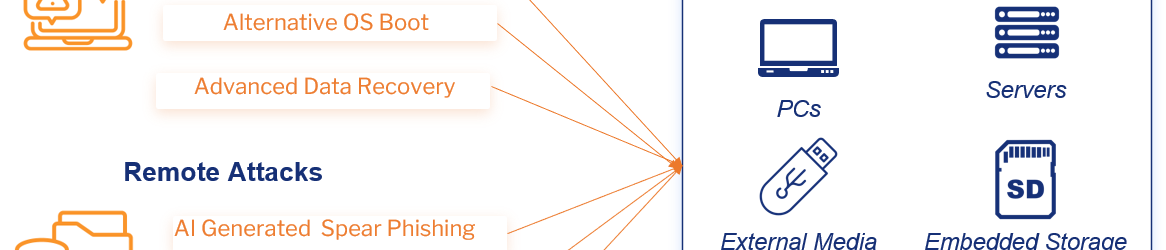
In a digital age where cybersecurity is as crucial as locking your front door, Senhasegura emerges as a beacon of innovation and security, transforming how organizations manage their most sensitive asset: passwords. The company’s latest enhancements to MySafe, its advanced password manager and privileged access management (PAM) solution, mark a […]