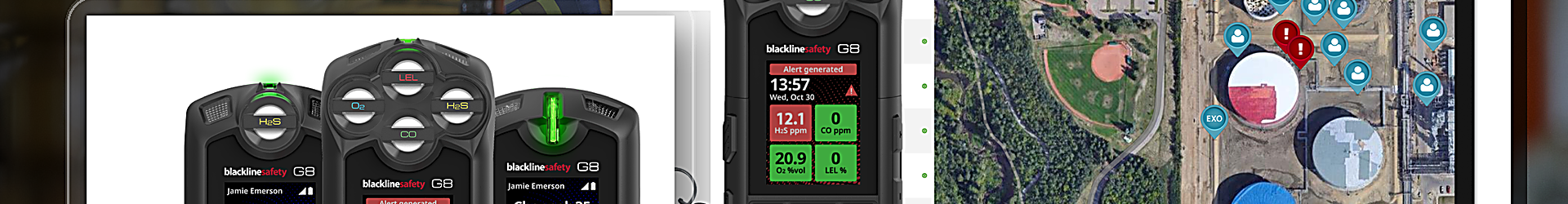
Identity theft can quickly turn into a nightmare scenario that ruins people’s credit and adds unwanted stress. Cybercriminals use artificial intelligence (AI) and more sophisticated methods than in the past to access sensitive information. Understanding the emerging trends in identity theft can help security professionals and individuals strengthen protections and […]