Access risk is an invisible liability that never shows up on balance sheets, shipping schedules, or vendor scorecards. It silently builds up through unmanaged accounts and unmonitored logins, stalling operations, straining supply chains, and eroding the trust that businesses depend on.
Identity and access management (IAM) is intended to reduce that risk. It’s foundational to security, governance, and continuity at scale, the true gateway to your operations. Yet, it’s often designed to secure employees and customers, leaving third-party access as an afterthought. That oversight is the modern equivalent of installing a firewall while ignoring insider threats.
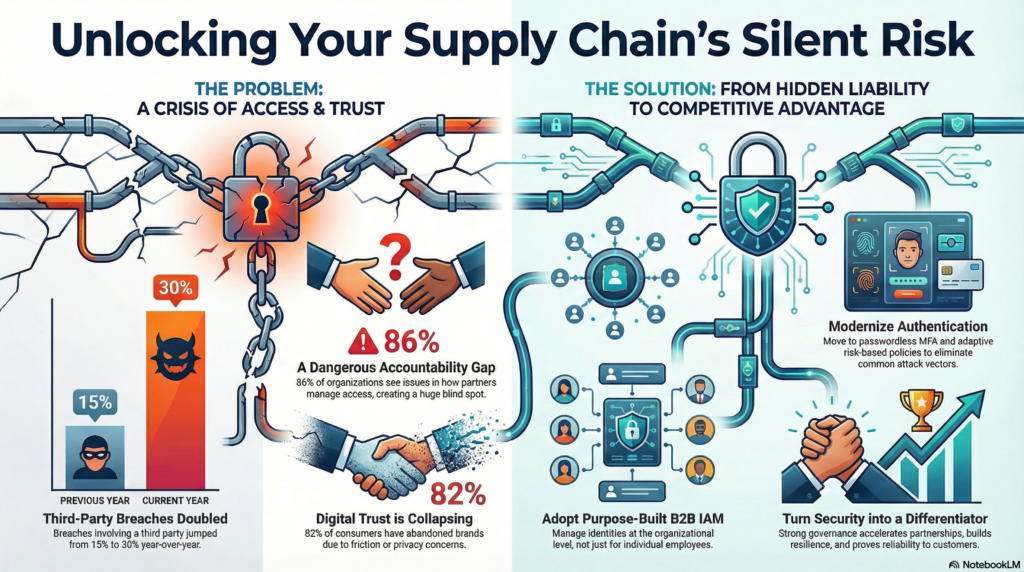
This is precisely the key takeaway from the latest Thales Digital Trust Index, Third-Party Edition. While third-party collaboration is essential to operations, user access management has long been underestimated as a driver of trust.
Meanwhile, cybercriminals exploit trusted vendor credentials and federation precisely because they’re rarely monitored with the same rigor as the workforce. The result is a dangerous illusion of security on the very systems that are intended to provide business agility and stronger collaboration.
Silent risks erupt into loud crises as breaches go undetected, drawing regulatory scrutiny and disrupting critical supply chains. Even established businesses aren’t immune and are effectively playing with fire.
Digital Trust is Collapsing
It’s no wonder that Digital Trust is already smoldering. Consumer behavior offers the clearest warning signal for B2B relationships. Another report indexing digital trust found that confidence in digital services is stagnant or declining across every sector, including the most highly regulated industries.
- 82% have abandoned a brand due to friction or privacy concerns.
- 31% have left over excessive data collection.
- 63% believe companies push security burdens onto users.
Consumer trust trends often foreshadow what will happen in B2B ecosystems. This erosion of confidence doesn’t just stop at consumer behavior; it cascades directly into enterprise supply chains, straining once-stable partnerships and elevating the perceived risks of doing business with you. Trust erosion slows deals, drives compliance costs and demands, and amplifies business risk.
Partners increasingly demand proof of mature IAM governance in contracts and renewals. Regulations such as DORA and PCI DSS 4.0 now treat vendor access risk as a core element of operational resilience.
How Excess Access Turns Supply Chains into Attack Vectors
Relationships with external vendors/partners are becoming a more frequent vector for breach events. In the 2025 Verizon DBIR, the percentage of confirmed breaches that involved a third party rose from 15% to 30% year over year. That’s amplified when nobody truly takes ownership of the risk.
Overprivileged accounts, stale federated identities, and flat trust models silently expand the attack surface. Credential stuffing and account takeover campaigns often go unnoticed until attackers pivot through trusted partners.
The Accountability Gap: Why Risk Stays Hidden
Accountability for third-party access is often undefined. Granular permission reporting, full lifecycle management, and continuous monitoring are often missing. Ownership of third-party risk is blurred, so breaches tied to external access create confusion instead of a clear response. Exceptions take the place of security and governance.
Cultural factors make it even worse: vendors push for exemptions to avoid friction, access grows organically without cleanup, and executives delay IAM overhauls to avoid disruption. The risk goes unchecked and unreviewed, but the impact of these inadequate practices is producing dissatisfaction.
The findings of the Thales survey are indicative:
- 31% of partners wait days for access, stalling business before it starts.
- 86% of organizations see issues in how partners manage access, extending risk beyond enterprise control.
- Half of users keep access long after they need it, and fewer than half receive the right access after a role change.
- There is little to no vendor participation or delegation of access control closer to the birthright.
It’s no wonder that confidence is also low: only 56% of organizations believe partners would disclose a breach promptly. Together, these gaps turn partner access into a blind spot that attackers know how to exploit.
Vendor Risk Assessments: A False Sense of Security
Most vendor assessments still measure compliance, not resilience, focusing on surface-level questions like “Do you use MFA?” or “Do you have SSO?” but produce documents that are seldom referenced again.
Critical details such as authentication flow design, API permissions, token storage, privilege tiers, or role separation go unexamined. The result is a false sense of security because they measure what’s easy to ask, not what actually stops breaches.
The user experience also suffers. 96% of third-party users face login issues, wasting nearly an hour each month. 69% of verification processes are digital but inconsistently owned, slowing vendor onboarding. 40% of users reset passwords once or twice a month, clinging to outdated and phishable methods.
Assessments miss these realities, leaving the most common pain points and attack vectors unaddressed. As attackers automate, exploit speed and cost are falling, widening the gap between compliance and protection.
Solution Path: Treat Access as a Board-Level Metric
Strengthen your security posture with purpose-built B2B Identity and Access Management (IAM). Traditional IAM systems were designed for workforce users, not for the scale and interdependence of modern third-party ecosystems. B2B IAM manages identities at the organizational level, supporting partner hierarchies, shared responsibilities, and relationship-based access that adapts as collaborations evolve.
Modernize authentication with passwordless MFA and adaptive risk-based policies, and demonstrate transparency through data sovereignty, as 37% of consumers report higher trust when data residency is clearly communicated.
From Invisible Threat to Strategic Differentiator
Access is now the most overlooked source of enterprise exposure, especially across interconnected supply chains. Traditional controls were built for predictable environments and cannot adapt to the pace of modern collaboration. Closing that gap requires new capabilities that bring visibility, accountability, and trust to every external connection.
Organizations that invest in these capabilities gain more than security. They build resilience, accelerate partnerships, and demonstrate reliability to customers, regulators, and suppliers alike. By elevating access from a technical safeguard to a business enabler, companies transform what was once a hidden liability into a clear competitive advantage.
About the Author
Jose Caso, B2B IAM at Thales, is a seasoned product professional with over 15 years of experience in software development, product management, and product marketing. He specializes in aligning technical and business goals to deliver solutions that meet evolving client needs. With a background spanning physical security, cybersecurity, and enterprise solutions, Jose focuses on driving innovation that keeps businesses competitive in a dynamic market.
Additional Resource
Video Overview
Follow Brilliance Security Magazine on LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information. BSM is cited as one of Feedspot’s top 10 cybersecurity magazines.



