By Paul Nicholson, Senior Director, Product Marketing at A10 Networks.
The world has been battling the COVID-19 pandemic for the last several years, and threat actors have taken advantage of the disruption to ramp up cyber-attacks at an accelerated rate. We are slowly transitioning to a more normal operating environment. Yet, the cyber world is continually engulfed in a pandemic of cyber-attacks.
A10 Networks’ security research team has tracked these developments over several years, observing and recording the origins, trends, and behavior of DDoS weapons.
A DDoS weapon can be defined as any set of computers, servers, and/or IoT devices that can potentially be repurposed to be used in DDoS attacks. These weapons can range from IoT devices that can be leveraged to create botnets for on-demand attacks to legitimate services open on the internet, like DNS resolvers and NTP servers that are used to amplify and reflect attack traffic.
In the last year, there were many interesting developments in cyber-criminal activity. Stories have ranged from attackers leveraging the once obscure, but now notorious, Log4j vulnerability, to Microsoft mitigating one of the largest DDoS attacks ever recorded. The Apache Log4j vulnerability is a clear example of how software that is used by millions of systems around the globe can be used in the creation and propagation of botnets used in DDoS attacks, while also controlling them.
Cyber Warfare and the Use of DDoS Attacks
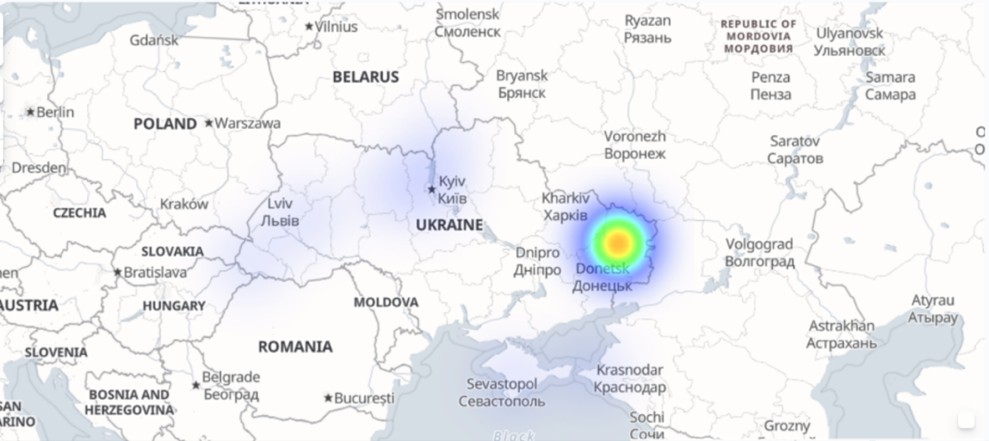
At the beginning of 2022, the Ukraine-Russia conflict took a turn for the worse, evolving into an all-out war. At the outset of the ground war, A10’s security research team observed several cyber-attacks targeting Ukraine government networks and infrastructure. These weren’t random attacks designed to wreak havoc. They were large and well-coordinated attacks designed to support the ground offensive through confusion and service disruption.
For example, right before the war began, A10 Networks observed two major attacks that occurred on specific targets related to the Ukrainian government and infrastructure. These were among multiple attacks of varying sizes and intensities targeting multiple locations throughout Ukraine.
Global Spike in Available DDoS Weapons
In the latest research, A10’s security research team recorded a significant spike in the number of potential DDoS weapons available for exploitation in 2021 and early 2022. The total number of DDoS weapons, which was previously recorded at 15 million, has grown by over 400,000 or 2.7 percent in a six-month period. These potential weapons include botnets and drones, and amplification weapons. I’ll dig deeper into each of these categories below.
Botnets and Drones: Readily Available, Easy to Expand
Botnets can be created quickly for ad-hoc use in attacks, with numbers swelling to hundreds of thousands. Because of this characteristic, it is critical to keep a steady watch on, not just bot behavior, but also the mechanisms by which these botnets are created.
The number of total bots observed by A10 Networks in 2021 was lower by almost eight percent in comparison to the previous year. These numbers are highly volatile. Increases or decreases in botnets generally can be attributed to the following factors:
- The growth of IoT and availability of new IoT devices
- New vulnerabilities and CVEs exploited by attackers
- Large-scale security updates to patch CVEs in IoT devices
- Botnet take-downs
Successful vigilante or government-sponsored botnet take-downs can be critical in reducing the available weapons used in attacks. A service provider in India experienced a spike in botnet activity during the second half of 2020, making up 26 percent of the total number of global botnets observed by A10’s research team. These systems went offline soon after they were discovered. This was either entirely or in part a result of a vigilante group that claimed to have taken these systems down due to the service provider’s inaction.
In total, for all of 2021, China remained at the top of the list of countries that hosted the most DDoS botnets, with 34 percent of the global total in H2 2021. This was followed by India and the United States at 10 percent and six percent, respectively, in the same time period.
Are Amplification Attacks Still a Viable Method of Attack?
The research team tracked approximately 15 million unique potential amplification weapons systems in 2021. Clearly, they remain a viable method, and are linked to all the record-breaking attacks. The Simple Service Discovery Protocol (SSDP) remained at the top of the list of amplification weapons, with approximately three million systems exposed to the internet. While the number decreased from 3.2 million in the previous reporting period, it remains a significant potential threat given its approximate 30x amplification factor.
Devastating attacks can come from any vector. The amplification factor of a certain protocol (for example, 30x for SSDP) shows its potential efficacy as a weapon, and attention should be paid to tracking it. A10 saw an increase of over 100 percent, year-over-year, in amplification weapons that weren’t on the list of the top-five most used. This includes relatively obscure protocols, like Apple Remote Desktop (ARD), which was leveraged in the Ukraine-Russia conflict or Connectionless Lightweight Directory Access Protocol (CLDAP). The latter played a key role in the extremely large 2.3 Tbps AWS attack in 2020.
Protecting Infrastructure Against DDoS Attacks
Despite press coverage of extremely large DDoS attacks, it’s been a prevalent trend the last few years for attackers to focus on smaller attacks launched persistently over time. In fact, Microsoft reports that over 75 percent of DDoS attacks lasted for 30 minutes or less, allowing most of these attacks to fly under the radar and slowly drain the resources of victims’ machines and networks.
That said, the notoriety and capabilities of large-scale DDoS attacks cannot be diminished. In fact, while large-scale attacks might not occur as frequently as their low-volume, high-frequency cousins, they still make headlines a few times a year and cause damage to systems, business services, and reputations. In fact, Microsoft mitigated one of the largest DDoS attacks in late 2021, which had a throughput of 3.47 Tbps and a rate of 340 million packets per second, targeting an Azure customer in Asia.
Clearly, cyber-attacks, including state-sponsored attacks, are unavoidable, and will continue to intensify. DDoS attacks will continue to be used as tools of distraction, disruption for financial gain, or to make ideological statements. This year, there is clear evidence that closely coordinated cyber-attacks are being used to complement a physical confrontation on the ground in the Ukraine-Russia conflict, which has sent shockwaves to other organizations charged with safe-guarding critical digital infrastructure around the world, both in the government and the private sectors. We see this against the backdrop of the growth in the size and intensity of DDoS attacks, as well as the number of weapons that are readily available for use in these attacks.
A proactive approach to DDoS defense is essential to ensure critical services and infrastructure are protected. This approach should be based on the principles of Zero Trust so that malicious activity can be stopped before turning critical infrastructure and devices into DDoS weapons, as part of a botnet, or by unwittingly participating in an amplification and reflection attack. Zero Trust, with its “never trust; always verify” approach, can enable organizations to be proactive, rather than reactive, in their defense strategies. In addition, employing modern techniques as part of your Zero Trust planning for DDoS defense using threat intelligence, multiple levels of automation, and AI/ML can effectively protect your infrastructure, as well as the public internet, from devastating attacks.
Paul Nicholson brings 25 years of experience working with Internet and security companies in the U.S. and U.K. In his current position, Paul is responsible for global product marketing, technical marketing, and analyst relations at San Jose, Calif.-based security, cloud and application services leader A10 Networks. Prior to A10 Networks, Paul held various technical and management positions at Intel, Pandesic (the Internet company from Intel and SAP), Secure Computing, and various security start-ups.
.
Follow Brilliance Security Magazine on Twitter and LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information.


