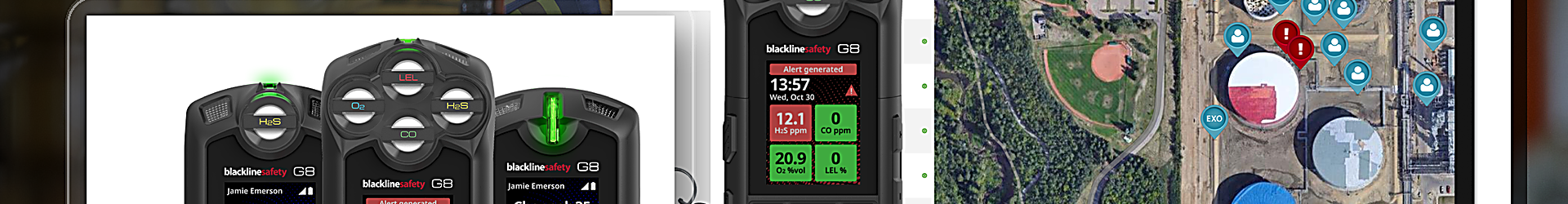
Cybersecurity experts work hard to make encryption stronger. As data becomes more readily available to companies, information security teams must adopt the latest tools in encryption. That’s because cybercriminals are finding new ways to steal their information. As hacking increases in sophistication, cybersecurity experts must find new ways to secure […]