Michael Silbernagel, Senior Security Analyst at SysGen
Businesses are currently dealing with an increasing rate of data within their organization, from confidential client information to internal documents that are relied upon for operation efficiency, businesses have a growing need to strengthen their cybersecurity protocols. Today, businesses face three key security issues: how to protect data while keeping it confidential, retain its integrity, and ensure its availability to those that need it. Together these three issues create the CIA triad of Cybersecurity. A significant threat to this concept is social engineering, a method of cyberattack that seeks to gain access to data while composing or ransoming the organization at the end of the attack.
Social Engineering and Cybersecurity
Social engineering is arguably the biggest cybersecurity threat to businesses today, as it is at the root of 98% of cyberattacks. This alarming statistic prompts business owners and cybersecurity experts alike to consider the impact of social engineering and seek out innovative solutions to protect businesses. In addition, social engineering threatens data confidentiality, integrity, and availability because these schemes work to gain access to accounts and manipulate and hold ransom information and data.
What is Social Engineering?
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. Effectively, social engineering attacks use human interaction to manipulate individuals into comprising or gaining access to an organization’s computer system. Social engineering is an umbrella term that encompasses many types of threats. Social engineering can take the form of pretexting, baiting, shoulder surfing, dumpster diving, malware, and, most commonly, phishing attacks.
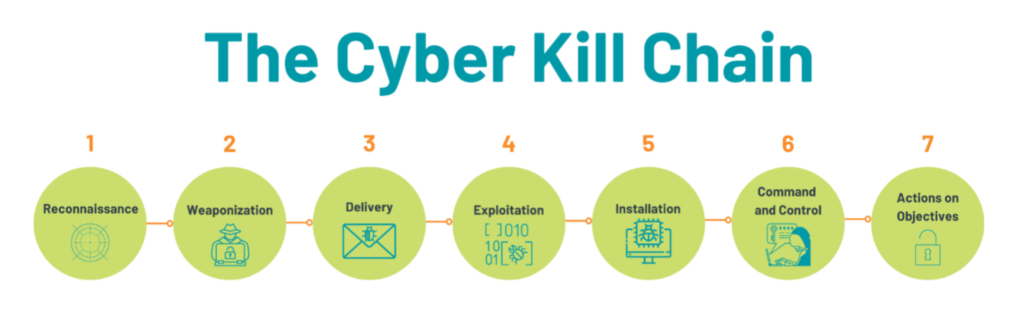
The Cyber Kill Chain: A Social Engineering Roadmap
To understand these issues, one must first understand the Cyber Kill Chain. The cyber kill chain outlines the process of most phishing attacks. With this type of social engineering, a wide net is cast, sending thousands of emails at once, and if all bodes well for the cybercriminal, they will receive a few bites. Typically, they will target an organization like a bank or a healthcare
provider. First, they study and learn about the organization in the reconnaissance phase. Then, develop and weaponize an email and send it out for delivery. Assuming an end-user takes the bait, the cybercriminal can exploit the information gained and install a trojan horse or malware, gaining access to the on-prem computer. Then with this power, they can act on any goals they may have, such as taking down websites and stealing client information.
Why Do We Need Social Engineering Solutions?
As previously noted, an overwhelming majority of cyber threats are rooted in information or access gained from social engineering attacks. Therefore, businesses must act in social engineering solutions to dramatically reduce the risk of cyber threats.
What Types of Issues Can Be Addressed Through Social Engineering?
Training and Education
Businesses can protect themselves and their employees from Social Engineering – specifically regarding phishing attacks- by regularly providing their staff with Cybersecurity Awareness / Internet safety training. This training is essential because it teaches employees how to identify phishing emails, viruses, malware, and other important information they need to know to keep themselves and the organization safe and secure on the internet.
Within training and education, there are three key mechanisms to ensure that security is at the top of your employees’ minds. Firstly, peer-to-peer training is critical to creating an engaging environment with opportunities for questions and learning. The second is online security awareness training, which involves testing employees with fake social engineering techniques, such as phishing emails. The third mechanism is print materials, including security bulletins and office-space posters. Through this, we can create a conscious and subconscious awareness of Cybersecurity.
In every organization, Cybersecurity needs to be everyone’s responsibility.
Technical Controls
Training employees is critical to protecting your organization, but layered security also leverages the power of technology to protect it. For example, Proofpoint is an email protection system that blocks spam, phishing, and viruses from reaching your inbox. This system analyzes emails and traces their origin to catch fake emails. Depending on your organization’s email system, you may have an additional layer of protection with Microsoft 365’s built-in security. These technical controls are simple yet effective. Each layer of security reduces the likelihood of a dangerous email making it into your inbox. This security measure can be taken a step further; businesses that leverage the services of managed service providers can exploit the knowledge and resources of cybersecurity experts. For example, SysGen’s Enhanced Security Services (ESS) works proactively to protect your organization by developing technical controls, educating your employees, and finding security gaps in your organization, ensuring you have a layered approach to security that works to eliminate threats before they become issues.
In addition to technology that analyzes and filters our spam communications, it is also crucial that organizations implement multi-factor authentication (MFA) controls. In a phishing attempt, an unsuspecting and untrained user may deceive a malicious email with a link or attachment that initiates the attack and allows the cybercriminal to access their account. During these attempts, MFA becomes critical because it prevents single login sign-ins. As a result, the cybercriminal would not be able to use the login credentials gained in the attack alone, thus thwarting the attack.
What Makes These Solutions Stand Out?
These mechanisms are optimal solutions as they address the principal vulnerabilities that cybercriminals attempt to exploit through social engineering. As discussed earlier, social engineering is the manipulation of humans through technology to reveal or compromise information and data. By focusing your efforts on training your employees, we can dramatically reduce the threat of manipulation that cybercriminals work to exploit.
In What Situations Could These Solutions Be Useful?
Cybersecurity is a constantly changing and evolving field with many different moving parts. For this reason, it is difficult to pinpoint specific solutions as blanket offers. However, when looking holistically at Cybersecurity, we know that educating employees to become aware of and learn to thwart cyber-attacks is critical.
Social Engineering Solutions and Risk Mitigation
Ultimately, the best way to prevent social engineering attacks is to leverage a proactive strategy that takes a layered approach to filter out step-by-step threat attempts like phishing emails. Due to the fact that social engineering relies on manipulating humans, training people is the best way to prevent it. Technology adds a layer of protection and support, but there are still gaps, and therefore we need to train and educate our first line of defense, our employees, to catch and stop these attacks.
Michael Silbernagel is a Senior Security Analyst at SysGen, a client-focused IT consulting organization for small to mid-sized businesses. Michael is the lead of the cybersecurity consulting and incident response (CSIRT) team and the creator of SysGen’s Enhanced Security Services (ESS), a holistic and comprehensive cybersecurity offering that focuses on People, Technology, Policy, and Process.
.
Follow Brilliance Security Magazine on Twitter and LinkedIn to ensure you receive alerts for the most up-to-date security and cybersecurity news and information.